This section describes how to set the TDE master encryption key for the container database (CDB) and pluggable databases (PDBs).
To set the encryption key at the CBD level:
Switch to the CDB level and make sure the session is correct:
show con_name
This should return CDB$ROOT.
Create the encryption key:
administer key management set key using tag 'master key' identified by SuperSecretPass with backup using 'masterbackup';
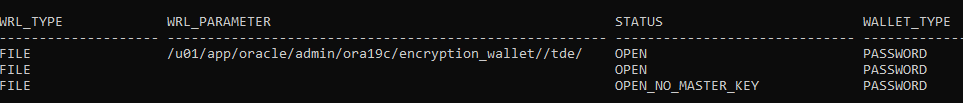
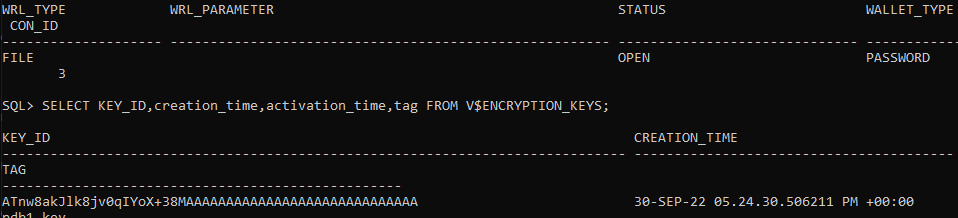
Check the keystore status.
set pages 300
set lines 300
col WRL_PARAMETER for a55
select * from v$ENCRYPTION_WALLET;

Check that the key was generated.
col TAG for a50
col CREATION_TIME for a40
col ACTIVATION_TIME for a40
SELECT KEY_ID,creation_time,activation_time,tag FROM V$ENCRYPTION_KEYS;
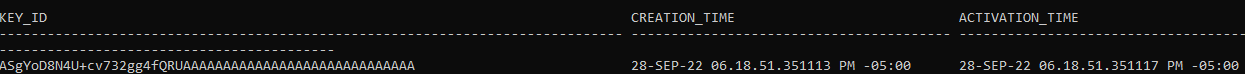
Check that the files were created.
ls -ltr /u01/app/oracle/admin/ora19c/encryption_wallet/tde
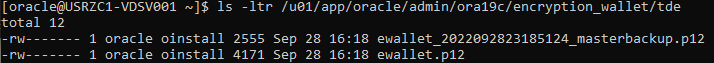
To set the key at the PDB level:
Switch to the PDB level.
Verify that the key does not exist.
alter session set container=ORA19C_PDB01;
select * from v$ENCRYPTION_WALLET;
SELECT KEY_ID,creation_time,activation_time,tag FROM V$ENCRYPTION_KEYS;
Now set the key.
administer key management set key using tag 'pdb1 key' identified by SuperSecretPass with backup using 'masterbackup2';
select * from v$ENCRYPTION_WALLET;
SELECT KEY_ID,creation_time,activation_time,tag FROM V$ENCRYPTION_KEYS;
ls -ltr/u01/app/oracle/admin/ora19c/encryption_wallet/tde
This should return one more e-wallet. It is also a good practice to validate successful database key creation in the alert log file.